Wireshark is commonly used network protocol analyzer for Unix and Windows, it’s available for free download from project homepage, http://www.wireshark.org/. This was tested on RouterOS v6.38.5 (mipsbe), but it should work mostly the same everywhere. I was using MacOS Sierra 10.12.5 Beta (16F67a) and Wireshark 2.2.1 (v2.2.1-0-ga6fbd27 from master-2.2), on a MacBook pro using a 802.11 ac card.
How do I get it working?
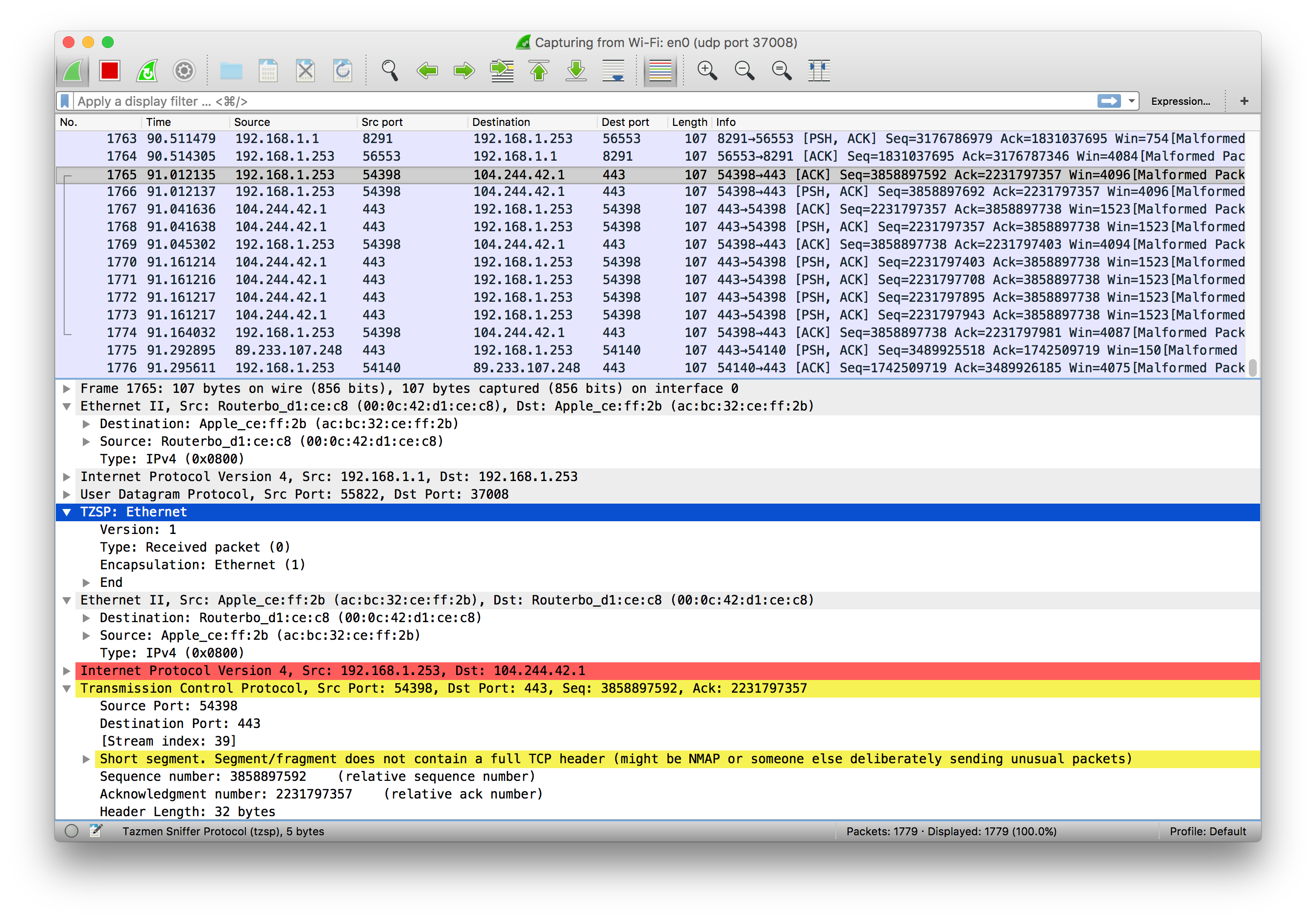
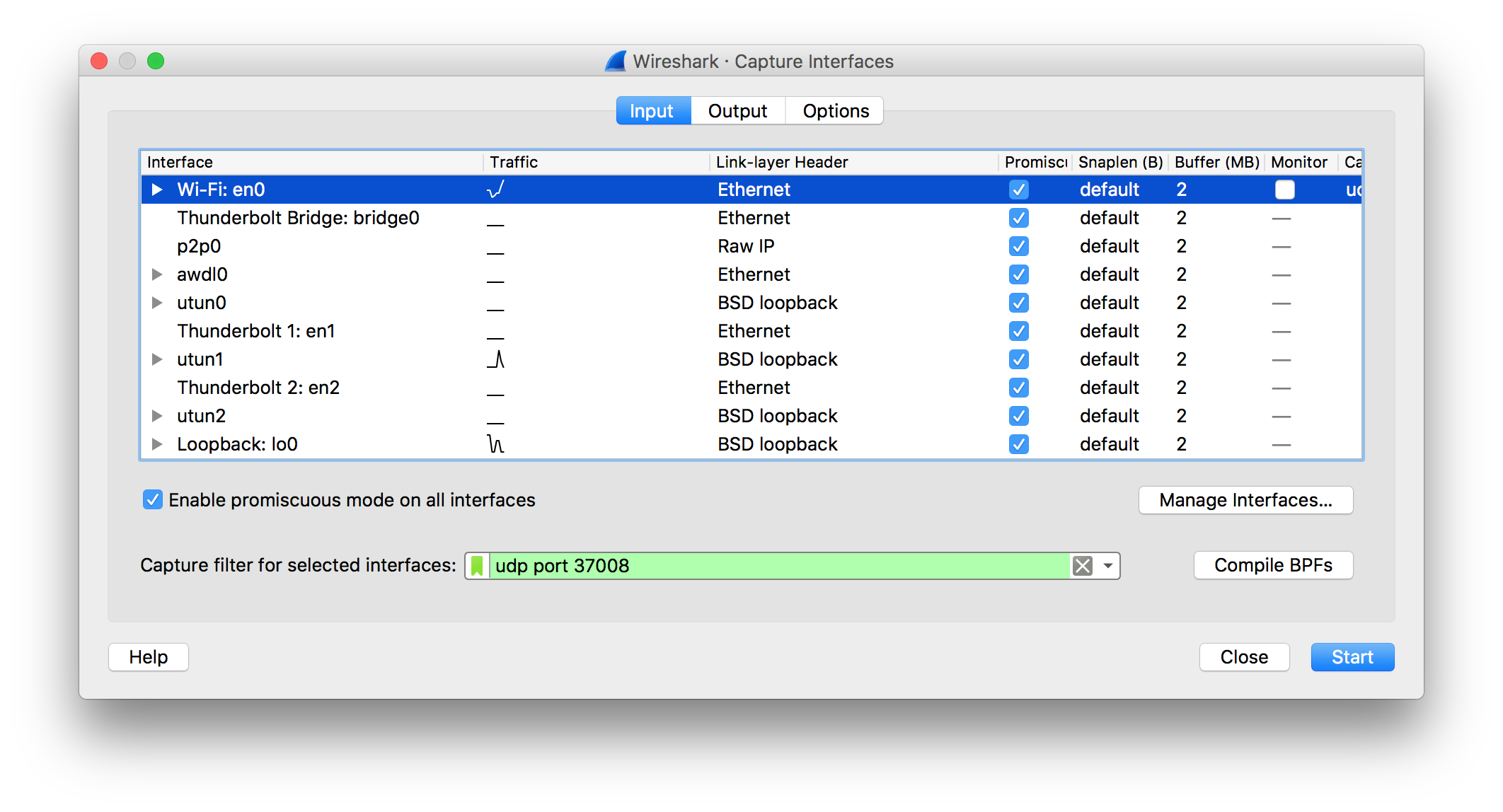
First, launch Wireshark, and start a capture on the interface that’s connected to the MikroTik box. This may be a wired or wireless interface. To accept sniffer TZSP (TaZmen Sniffer Protocol) stream, you have to set the configuration.
- To accept only TZSP traffic, Capture Filter like this can be used
udp port 37008
- Make sure you accept UDP in Wireshark (as TZSP uses UDP to transport data);
- You may need to disable WCCP protocol in Wireshark (Analyze/Enabled Protocols), as that collides with TZSP and by default frames may be considered WCCP, not TZSP;
- For streaming wireless sniffer captures (interface wireless sniffer), make sure you have newest Wireshark and newest RouterOS.
Next, configure the sniffer tool on the MikroTik box.
/tool sniffer set streaming-enabled=yes set streaming-server=ip.of.wireshark.box set filter-stream=yes set filter-interface=bridge1
Finally, start the sniffer.
/tool sniffer start
That’s it! You should start to see frames streaming in on the Wireshark display. Don’t forget to stop the sniffer later, otherwise it will keep running until rebooted.
Leave a Reply